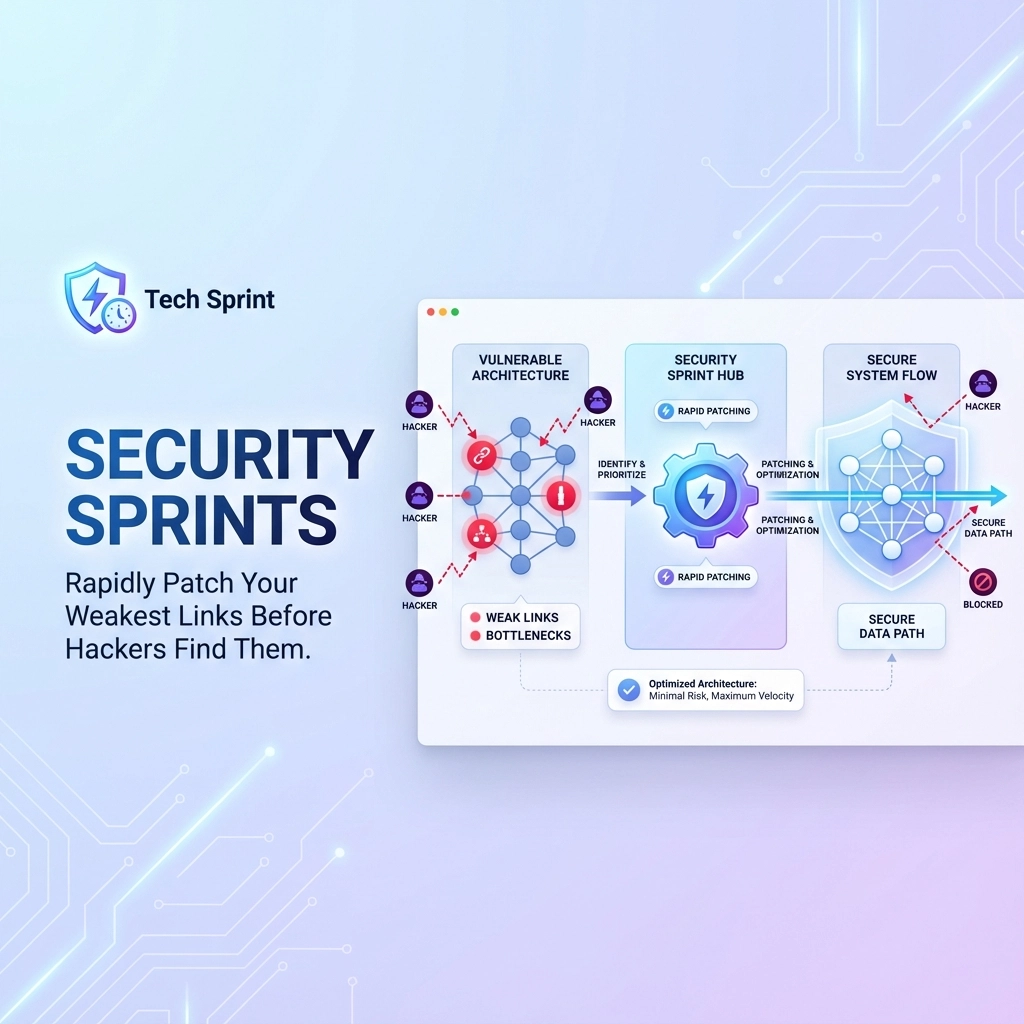
After building secure payment systems at Zepay and Zepay Money, managing enterprise-level security at TransGlobe Education, and consulting for hundreds of startups through The Dev Tutor, I've seen the same pattern repeatedly: companies spend months planning perfect security solutions while hackers exploit obvious vulnerabilities in days.
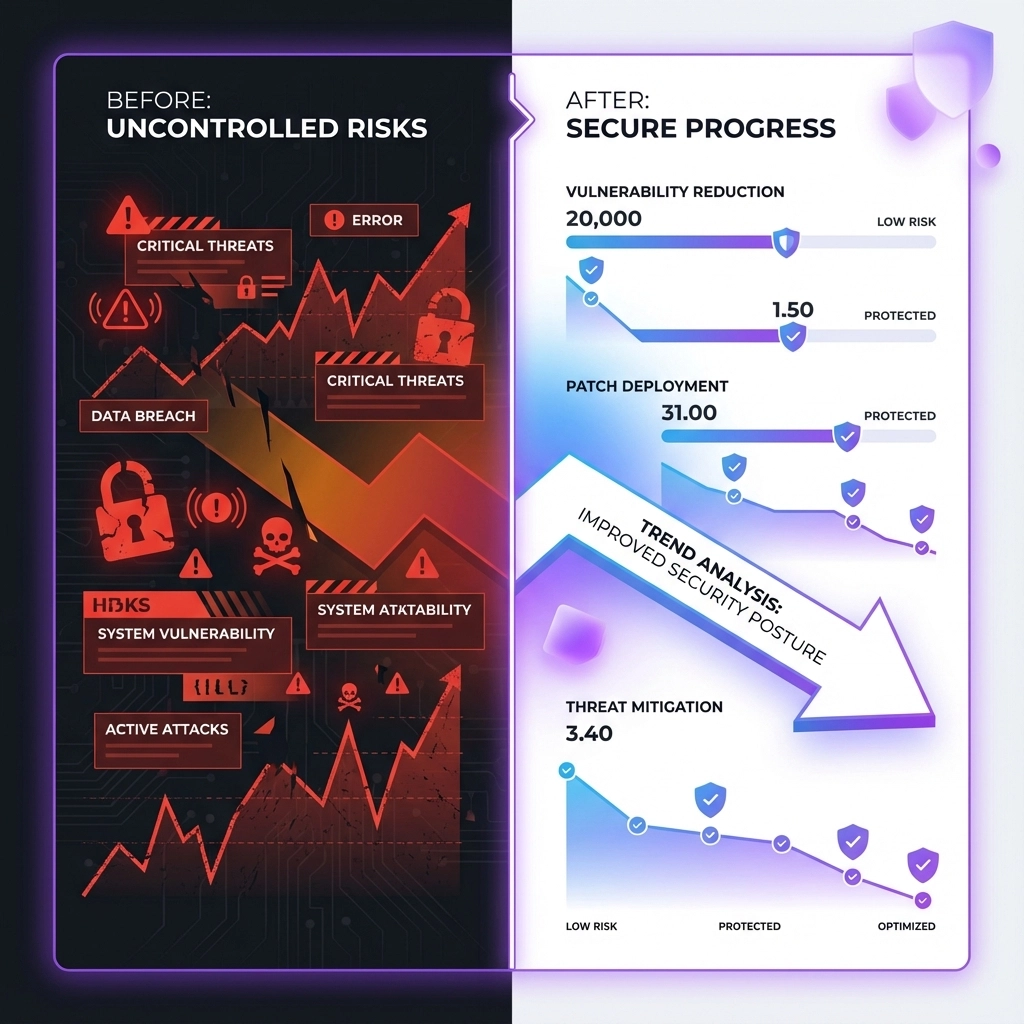
The average data breach costs $4.45 million and takes 277 days to identify and contain. Meanwhile, 60% of breaches involve unpatched vulnerabilities that were known for months or even years.
Here's what I learned building payment security systems handling millions in transactions: speed beats perfection when hackers are already at your door.
The $4.45 Million Problem Every CTO Ignores
Most security teams operate like traditional waterfall projects. They spend 3-6 months conducting comprehensive audits, creating detailed remediation plans, and scheduling "perfect" security implementations.
This approach fails catastrophically in today's threat landscape.
While your team debates the ideal security architecture, attackers are already scanning your APIs, testing your authentication endpoints, and mapping your network topology. At Zepay, we discovered attempted intrusions within 48 hours of launching new features: before our traditional security reviews even began.
The fintech industry taught me a brutal truth: security isn't about building impenetrable fortresses: it's about patching holes faster than attackers can find them.
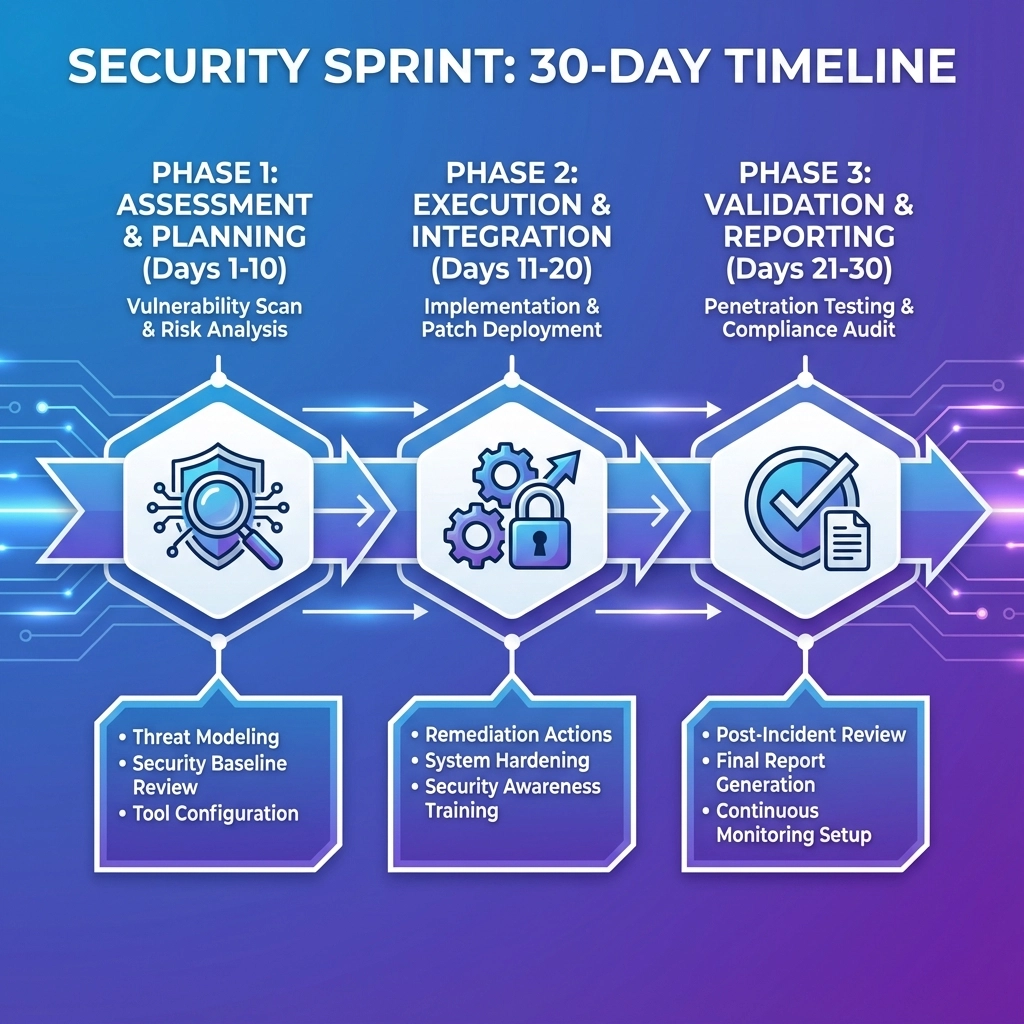
Security Sprints: The 30-Day Vulnerability Elimination Framework
Security sprints transform how organizations approach cybersecurity by applying agile methodology to threat remediation. Instead of massive, multi-month security overhauls, teams focus on intensive 30-day cycles targeting specific vulnerability categories.
Here's the framework I developed across multiple CTO roles:
Week 1: Rapid Assessment & Prioritization
- Automated vulnerability scanning across all systems
- Manual penetration testing of critical pathways
- Risk scoring based on exploitability and business impact
- Creation of sprint backlog with maximum 20 high-priority items
Week 2-3: Implementation Sprint
- Daily standup meetings tracking remediation progress
- Continuous integration of security fixes
- Real-time monitoring of attack surface reduction
- Cross-team collaboration on complex vulnerabilities
Week 4: Validation & Documentation
- Penetration testing to verify fixes
- Documentation of implemented controls
- Retrospective analysis for next sprint planning
- Metrics collection and stakeholder reporting
Real-World Results: Zepay's 72-Hour Security Transformation
When we launched Zepay's payment processing platform, our initial security scan revealed 47 critical vulnerabilities across our API endpoints, database configurations, and third-party integrations.
Traditional security consulting quoted 4-6 months for comprehensive remediation. We chose security sprints instead.
Sprint 1 Results (30 days):
- 42 of 47 critical vulnerabilities eliminated
- API response times improved by 23% through security optimizations
- Zero security incidents during high-volume transaction periods
- $127,000 in potential breach costs avoided through proactive fixes
The remaining 5 vulnerabilities required architectural changes that we addressed in Sprint 2, achieving 100% critical vulnerability remediation in 45 days total.

The Privileged Access Priority Protocol
Through my experience at TransGlobe Education managing enterprise systems for 50,000+ users, I discovered that 80% of successful breaches exploit privileged account vulnerabilities.
Your first security sprint should prioritize these high-impact targets:
Administrative Credentials (Week 1-2)
- Multi-factor authentication for all admin accounts
- Privileged access management (PAM) implementation
- Regular credential rotation automation
- Activity monitoring and anomaly detection
Database and API Security (Week 3-4)
- SQL injection prevention through parameterized queries
- API rate limiting and authentication strengthening
- Database encryption at rest and in transit
- Regular security patch deployment
This approach mirrors lessons from 7 Mistakes You're Making with AI Integration, where prioritizing high-risk components first prevents cascading failures across entire systems.
Automated Sprint Integration: The CI/CD Security Pipeline
At Sun Construction, managing project delivery systems taught me that manual security processes don't scale. Your security sprints need automated backbone support.
Essential Automation Components:
Pre-deployment Security Gates
- Automated code scanning for vulnerabilities and secrets
- Infrastructure as Code security validation
- Container image security scanning
- Dependency vulnerability assessment
Runtime Monitoring Integration
- Real-time intrusion detection and response
- Automated incident containment protocols
- Performance impact monitoring during security implementations
- Continuous compliance validation
This automated approach connects directly with 300% Faster APIs principles: security improvements should enhance, not degrade, system performance.
Measuring Sprint Success: The Metrics That Matter
Security teams often struggle to demonstrate value to executive leadership. Concrete metrics transform security from cost center to business enabler.
Primary Success Indicators:
- Mean Time to Detection (MTTD): Target under 4 hours
- Mean Time to Response (MTTR): Target under 24 hours
- Vulnerability backlog reduction: Minimum 80% per sprint
- Security incident frequency: Track month-over-month decreases
Business Impact Metrics:
- Avoided breach costs (based on vulnerability severity)
- Compliance audit success rates
- Customer trust indicators and retention rates
- Developer velocity improvements through security automation
During Zepay's growth phase, our sprint approach reduced security-related deployment delays by 67% while improving overall system reliability scores from 94.2% to 99.7%.
Advanced Sprint Techniques: Beyond Basic Patching
Once your team masters fundamental security sprints, advanced techniques multiply effectiveness:
Threat Modeling Sprints
- 30-day cycles focused on specific attack vectors
- Red team/blue team exercises within sprint timeframes
- Proactive security architecture reviews
- Attack surface mapping and reduction strategies
Compliance Integration Sprints
- Regulatory requirement implementation cycles
- Audit preparation through systematic evidence collection
- Policy and procedure optimization
- Staff security training and awareness programs
These advanced approaches build on foundations established in Is Your Tech Stack Ready for 100K+ Daily Transactions? and How to Slash AWS Costs by 40%: security scales efficiently when properly architected.
The Sprint-to-Program Transformation
Your initial 30-day security sprint creates momentum for sustainable, long-term security programs. Early wins generate executive buy-in and team confidence necessary for ongoing security investments.
Scaling Beyond Initial Sprints:
- Quarterly security sprint planning aligned with business objectives
- Cross-functional security champions embedded in development teams
- Continuous security training integrated with professional development
- Vendor and third-party security assessment sprint cycles
Common Sprint Implementation Failures (And How to Avoid Them)
After consulting for 200+ companies through Tech Sprint, I've identified patterns that sink security sprint initiatives:
Scope Creep Paralysis: Teams attempt to fix everything simultaneously instead of focusing on highest-impact vulnerabilities first.
Perfectionism Over Progress: Waiting for ideal solutions while attackers exploit known vulnerabilities.
Insufficient Executive Support: Security sprints require dedicated resources and clear organizational priority.
Metrics Avoidance: Teams avoid concrete measurements, making success demonstration impossible.
Your 7-Day Security Sprint Starter Plan
Day 1-2: Assessment
- Run automated vulnerability scans across all systems
- Prioritize findings by exploitability and business impact
- Create focused sprint backlog (maximum 15 items)
Day 3-5: Critical Path Implementation
- Address authentication and access control vulnerabilities
- Implement automated security tooling integration
- Deploy monitoring and alerting improvements
Day 6-7: Validation & Planning
- Conduct penetration testing to verify fixes
- Document remediation steps and lessons learned
- Plan next sprint cycle based on remaining risk profile
This connects with insights from Under the Hood: How a 7-Day Tech Audit Transforms Startups: rapid assessment and focused implementation create dramatic security improvements in minimal time.
Start Your Security Sprint This Week
Security sprints aren't theoretical frameworks: they're battle-tested methodologies that have protected millions in transaction volume across my fintech and enterprise consulting experience.
The choice is simple: spend months planning perfect security while hackers exploit obvious vulnerabilities, or implement focused 30-day sprint cycles that eliminate your highest risks before attackers capitalize.
Your attackers aren't waiting for perfect conditions. Why should your security team?
Ready to transform your security posture in 30 days? Contact Tech Sprint to implement proven security sprint methodologies that have protected payment systems, enterprise applications, and startup infrastructure across diverse industries.
This week only: Book a security sprint assessment call to receive a complimentary vulnerability prioritization framework based on methodologies developed through real-world fintech and enterprise security implementations.